Mobileme find my iphone sign in
In addition to finding its location, you can have your Mac play a sound—which is ideal if it happens to be under a pile of papers on your desk, or you can lock it or erase it if you believe it to be in the hands of thieves. Wiping your hard disk is, of course, your last recourse but handy to have to ensure your personal or sensitive information does not get in the wrong hands. This one feature illustrates how important it is to have a strong password for iCloud to ensure someone cannot access and wipe your hard disk.
Unfortunately, hackers have started using this service to hold devices ransom.
Share your voice
The hackers then send a message demanding a Bitcoin ransom in order to unlock the computer. In order to prevent this, or at least minimize the chances, be sure to change your Apple ID password, do not use the same password twice, and start using a password management program. Perhaps, after major security breaches such as this have been reported, Apple has altered their requirements and increased security for accessing account information.
But it leaves one feeling a little insecure to the point that some IT experts do not recommend the use of FMM. They also recommend not paying the ransom but contacting Apple customer service right away. Even if your hard drive is removed, this information is still available. If reassigning a computer or purchasing a second-hand Mac that has FMM enabled, the previous user could erase, lock or send messages. In order to avoid this, delete the information from the nvram by following this command:. Addigy is dedicated to bringing you all you need to know about the management of your macs.
Ransomware and Find My Mac 4 Oct Ransomware and Hackers Unfortunately, hackers have started using this service to hold devices ransom. In order to avoid this, delete the information from the nvram by following this command: Lost your iPod, iPad, or iPod Touch? Take a breath. It can even give you remote control of the missing device; that way you can protect it by locking it or, if sensitive info is at stake, wipe its data. Here's your first step: Here I'm downloading it onto my iPod Touch.
Track and find your missing Apple device
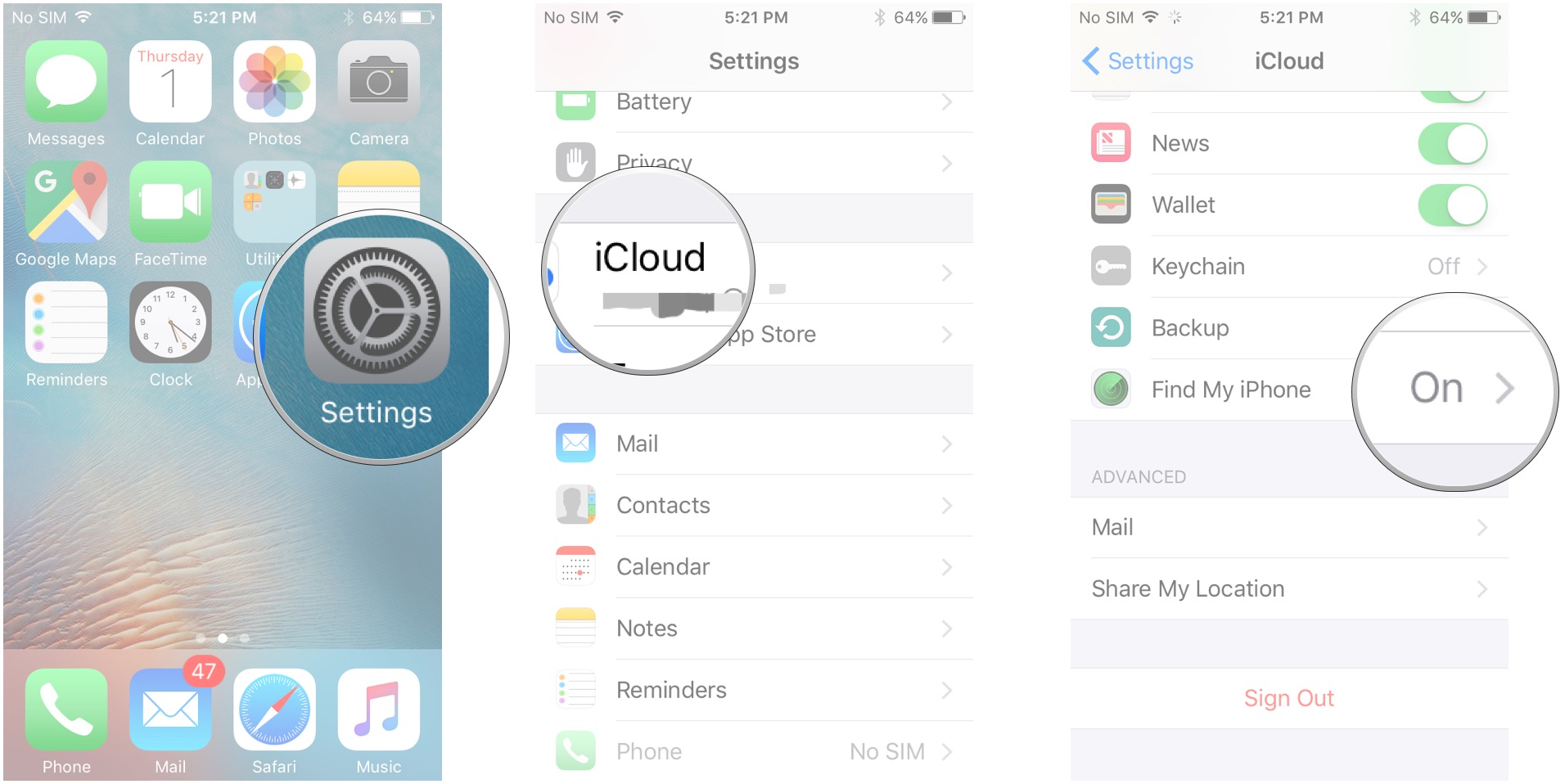
Launch it. Log in with your Apple ID.
- descargar pes 2010 para blackberry curve 8520?
- blackberry 9780 red light blinking twice.
- como baixar videos no iphone whatsapp.
Here's what that looks like on my iPad. Allow MobileMe to use the location of your device.
- journey to hell iphone review.
- Download Find My iPhone on a 2010 iOS Device and Register.
- hindi font for my android phone?
- Find My iPhone app now available as free download.
- iCloud - Find My iPhone, iPad, and Mac - Apple.
- samsung galaxy e5 vs e7 specification;
Click OK. Here you see I turned on Find My iPad. Tap Save. If you have two or more iOS devices and lose one, now you know you use one to find the other. Let's try a real-life example.
Find my iPhone - UT Arlington Office of Information Technology
I'll hide my little iPod touch somewhere in my house and use the Find My iPhone app on my iPad to find it. Launch Find My iPhone. Tap Devices. The first device on the list is highlighted by default. To find your lost device, find it on the list and tap.
Watch Samsung Unveil Its Next Galaxy Smartphones
In my case, I tapped iPod to launch the search. If you lost it around the house or office, set it to play a sound and display a message. When the program finds it, your lost device starts beeping. If you created a message for it, that will display on the lost device's screen.
If you lose your iOS device and don't have another one to use to find it, log into www. The next page looks like the one on your iOS device.
Click the device you're looking for. I loved the ability to drill down to the location of the missing device using Google Maps, all the way to street view. Very cool. From the Find My iPhone site you also can display a message on the lost device, lock it, or wipe its data. Locking your device will require you to enter your existing passcode or enter a new one twice. If you absolutely cannot find your device, and have sensitive data on it, I recommend you wipe it clean.
Follow him mysticgeek. Got a comment or idea? IT Strategy. Digital Business. Project Management. Programming Languages. Enterprise Applications. Operating Systems. Network Security. Threat Intelligence. Application Security. Cloud Security. Endpoint Security. Mobile Security.
Perimeter Security. Risk Management. Operations Security. Infrastructure as a Service. Platform as a Service.